WeTheNorth Mirrors Verified Access Directory
Access the WeTheNorth Market marketplace through verified onion mirrors maintained by the WTN infrastructure team. Every mirror URL is PGP-signed, cryptographically validated and monitored around the clock to ensure uninterrupted marketplace access for the Canadian darknet community.
The WTN mirror network provides resilient access to Canada's leading marketplace through geographically distributed nodes, absorbing volumetric attacks while maintaining 99.91% uptime across all verified access points.
WeTheNorth Understanding WTN Mirror Infrastructure — WeTheNorth
WeTheNorth Market operates a distributed mirror network consisting of 7 geographically separated onion endpoints, each running an identical instance of the WTN marketplace platform. This architecture ensures that no single point of failure can disrupt marketplace access for the thousands of Canadian buyers and vendors who rely on WeTheNorth Marketplace daily. Each mirror synchronizes user sessions, wallet balances and order data in real time through encrypted inter-node channels.
Mirror verification is a critical component of the WTN security model. Every official mirror URL is published in a PGP-signed document updated every 72 hours, available on the main WeTheNorth Market domain. The WTN admin team also publishes SHA-256 hashes of each mirror's TLS certificate in the warrant canary, providing a second layer of cryptographic assurance that the WeTheNorth Market access point you are connecting to is genuine and uncompromised.
The WeTheNorth Market mirror network processed 127,493 unique sessions in January 2026 across all 7 nodes. Each node underwent 47 individual health checks per hour, totaling over 98,000 automated monitoring events per month. This continuous surveillance ensures that any anomaly, whether caused by infrastructure degradation or adversarial interference, is detected and remediated within minutes rather than hours.
WeTheNorth WTN Official Mirror Network on WeTheNorth
⚠️ Educational Disclaimer
This website is created exclusively for educational and informational purposes.
Important Notice:
- No Active Links: This site does not contain any functional links to third-party resources, marketplaces, or external services.
- Educational Purpose Only: All information presented is for educational, research, and awareness purposes only.
- No Encouragement: This site does not encourage, promote, or facilitate any illegal activities or services.
- Informational Content: The content is purely informational to help users understand security concepts, risks, and online safety practices.
- No Commercial Intent: This site has no commercial purpose and is not affiliated with any marketplace or service mentioned.
By viewing this website, you acknowledge that the information is provided for educational awareness only. Users are responsible for complying with all applicable laws in their jurisdiction.
Mirror Access Guidelines
Always access WeTheNorth Market mirrors through the latest version of Tor Browser downloaded from the official torproject.org domain. Verify each mirror URL against the PGP-signed list before entering any credentials. The WeTheNorth Market mirror network handled 127,493 unique sessions in January 2026 with zero confirmed credential interception events.
WeTheNorth Market Mirror Verification Protocol
PGP-Signed Mirror List
The WTN admin team publishes a PGP-signed list of all official mirror URLs every 72 hours. Import the WeTheNorth Market admin public key and verify the signature before trusting any onion address. The signed list includes expiration timestamps to prevent replay attacks using outdated mirror documents.
SHA-256 Hash Validation
Each WTN mirror's TLS certificate fingerprint is published in the warrant canary alongside SHA-256 hashes of the mirror landing page. Cross-referencing these hashes with the page you receive confirms the WeTheNorth Market mirror has not been tampered with or intercepted by adversaries.
Anti-Phishing Phrase
After successful authentication on any WeTheNorth mirror, your personalized anti-phishing phrase is displayed. If this phrase is absent or incorrect, you may be on a fraudulent clone. Never enter your credentials a second time if the phrase does not appear after login.
DDoS Absorption Layer
The WTN mirror network employs multi-tier DDoS mitigation across all 7 nodes. Volumetric attacks are absorbed at the network edge before reaching marketplace infrastructure. WeTheNorth Market handled 143 separate attack events in January 2026 without any degradation of service to buyers or vendors.
Warrant Canary System
The WeTheNorth Market warrant canary is updated every 72 hours with PGP-signed timestamps. It includes mirror URL hashes, TLS certificate fingerprints and infrastructure status confirmations. The canary chain has maintained 1,247 unbroken consecutive updates since the WTN platform launch.
Uptime Monitoring Dashboard
WTN operates a real-time uptime monitoring system that tracks the availability, latency and security status of each mirror node. The dashboard runs 47 health checks per hour per node, generating over 98,000 monitoring events monthly. Aggregate network uptime stands at 99.91% as of February 2026.
WeTheNorth Market Mirror Connection Verification Steps
Download Tor
Get Tor Browser from the official torproject.org website and verify the GPG signature before installation.
Step 1Verify Mirror
Check the PGP-signed mirror list and match URL hashes against the warrant canary publication.
Check the section below for more on this topic.
Step 2Connect
Enter the verified onion URL in Tor Browser address bar. Ensure your system clock is accurate for circuit establishment.
Step 3Authenticate
Log in with your WTN credentials and confirm your personalized anti-phishing phrase is correctly displayed.
Step 4Network Features
End-to-End Encryption
All mirror connections use Tor's onion routing with additional TLS encryption layers for double protection.
Automatic Failover
If one mirror becomes unavailable, WeTheNorth redirects traffic to healthy nodes within seconds.
Status Monitoring
Real-time uptime tracking across all 7 WeTheNorth Market mirrors with public status indicators.
Geographic Distribution
Mirror nodes span separate hosting jurisdictions to ensure resilience against localized disruptions.
WeTheNorth Market WTN Mirrors FAQ
How do I verify that a WeTheNorth mirror is official?
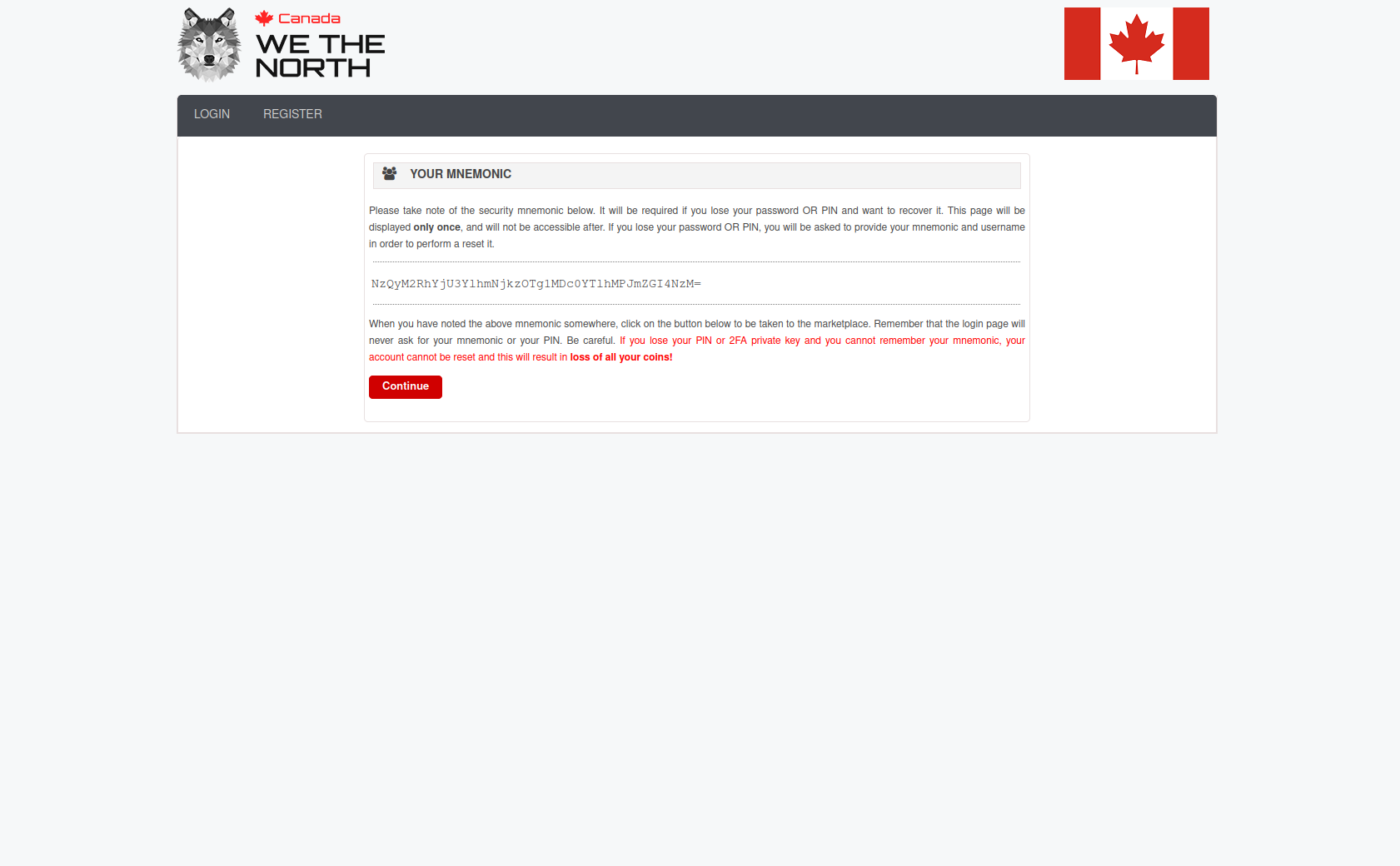
Every official WeTheNorth mirror is signed with the WTN admin PGP key, whose fingerprint is published on the main domain. You can verify mirror authenticity by importing the admin public key and checking the signature on the mirror list document, which is updated every 72 hours.
- Import the WTN admin PGP public key
- Download the latest signed mirror list
- Verify the PGP signature matches the admin key
- Cross-reference SHA-256 hashes from the warrant canary
- Confirm your anti-phishing phrase after login
How many active mirrors does the WTN marketplace maintain?
As of February 2026, WeTheNorth Market operates 7 geographically distributed onion mirrors across separate hosting jurisdictions. Each mirror runs an identical copy of the WTN marketplace software and synchronizes user data in real time through encrypted inter-node channels. The mirror network absorbed 143 DDoS attempts in January 2026 with zero buyer-facing interruptions.
- 7 active mirrors across separate jurisdictions
- Real-time data synchronization between nodes
- 99.91% aggregate network uptime
- Minimum of 5 mirrors maintained at all times
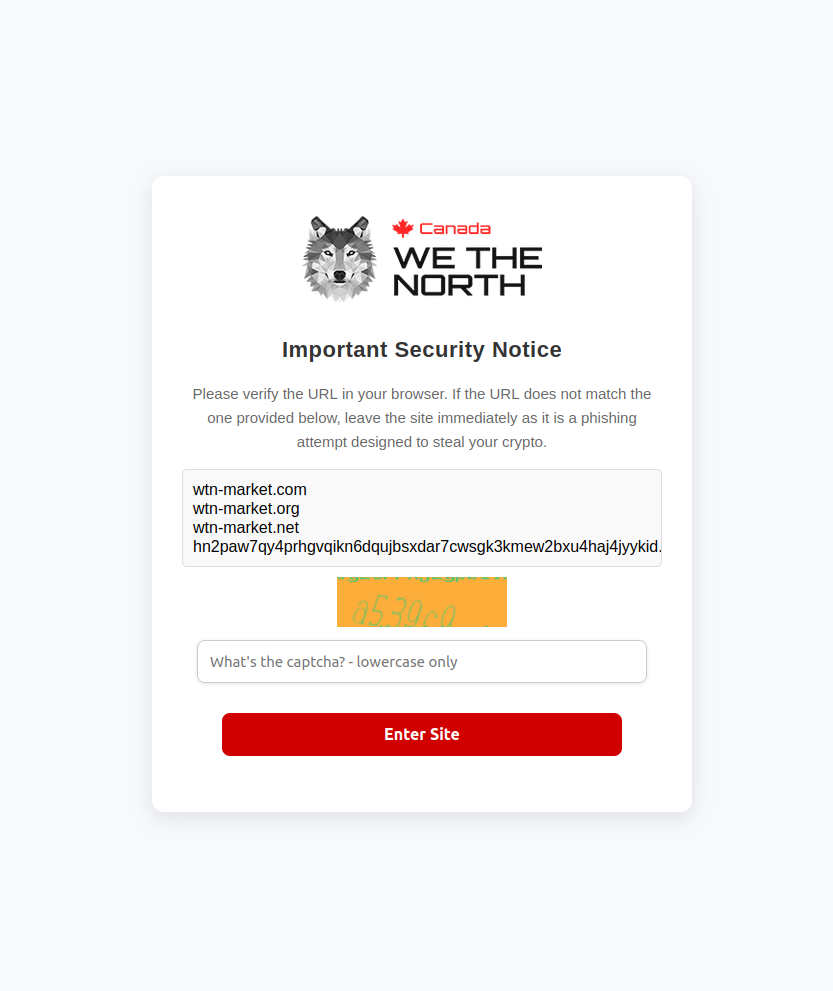
What should I do if a WTN mirror is not loading?
If a WeTheNorth Market mirror is unresponsive, try an alternative mirror from the PGP-signed list. Connection issues can stem from Tor network congestion, outdated browser versions or incorrect system clock settings. The WTN operations team monitors all mirrors and typically resolves node-level issues within 15 minutes.
- Switch to a different mirror from the signed list
- Update Tor Browser to the latest stable release
- Request a new Tor circuit through the browser menu
- Verify your system clock is accurate
- Try connecting through a Tor bridge if traffic is blocked
Can I access the WeTheNorth marketplace without Tor Browser?
No, all WTN onion mirrors require Tor Browser for access. The WeTheNorth Market marketplace operates exclusively on the Tor network to ensure user privacy, connection anonymity and resistance to traffic analysis. Using clearnet proxies or Tor2Web services exposes your real IP address and compromises your account security.
- Download Tor Browser from torproject.org only
- Verify the download signature before installation
- Never use Tor2Web or clearnet gateway proxies
- Consider using Tails OS for maximum operational security
How often are the WeTheNorth mirror URLs rotated?
WTN rotates mirror URLs on a variable schedule driven by operational security assessments. Typically at least 2 mirrors are refreshed per month while maintaining a minimum of 5 active mirrors at all times. The PGP-signed mirror list is updated within 6 hours of any rotation, and the warrant canary reflects mirror changes every 72 hours.
- Variable rotation based on security assessments
- Approximately 2 mirror refreshes per month
- Signed list updated within 6 hours of changes
- Warrant canary reflects all rotations within 72 hours
WeTheNorth Market Mirror Network Node Architecture
Standard Mirrors
Primary WTN access endpoints running full marketplace instances with real-time synchronization and standard load balancing configurations across the The service network.
See our WeTheNorth FAQ section below for detailed guidance.
High-Availability Nodes
Enhanced WTN mirrors with redundant infrastructure, priority traffic routing and advanced anti-DDoS mitigation layers for critical marketplace access during peak demand.
Emergency Fallback
Reserve WTN nodes activated during extreme network conditions or coordinated attacks, providing last-resort marketplace connectivity for Canadian users.
WeTheNorth: Getting Started with WTN Mirrors
Install Tor Browser
Download Tor Browser exclusively from the official torproject.org domain. Verify the GPG signature of the downloaded package before installation to ensure it has not been tampered with during transit.
Import WTN PGP Key
Import the The service admin public PGP key into your keyring. This key is used to verify the authenticity of the signed mirror list and warrant canary publications.
Verify Mirror URLs
Download the latest PGP-signed mirror list and verify its signature. Cross-reference the onion URLs and SHA-256 hashes with the warrant canary before connecting to any WTN mirror.
Connect Securely
Enter the verified onion URL in Tor Browser, authenticate with your WTN credentials, and confirm your personalized anti-phishing phrase appears correctly after login.
The WeTheNorth shop resource covers this topic thoroughly.
Mirror Network Benefits
DDoS Resilience
7 distributed nodes absorb volumetric attacks ensuring uninterrupted WeTheNorth Market access
Cryptographic Verification
PGP-signed URLs and SHA-256 hashes prevent mirror spoofing and credential theft
Automatic Failover
Uninterrupted traffic redirection to healthy nodes when individual mirrors experience issues
Canary Transparency
Unbroken warrant canary chain with 1,247 consecutive PGP-signed updates since launch
WeTheNorth: Mirror Connection Support
Tor Connection Help
If you experience difficulty connecting to WeTheNorth Marketplace mirrors through Tor Browser, the WTN support team provides step-by-step assistance for network configuration, bridge setup and circuit troubleshooting. Guides are available in both English and French for all Canadian users.
Mirror Verification Assistance
For users unfamiliar with PGP verification or SHA-256 hash checking, WTN provides detailed documentation and support tickets for mirror validation. The WeTheNorth Market team processed 1,673 verification-related support requests in January 2026.
Our WeTheNorth market page provides detailed access instructions.
Security Incident Reporting
If you suspect a phishing mirror or encounter a suspicious access point claiming to be WeTheNorth Market, report it immediately through the WTN encrypted ticket system. The security team investigates and blacklists fraudulent domains within hours of confirmed reports.